BGP FlowSpec
BGP FlowSpec
RASCOM is offering to their customers a set of tools protecting their networks against different types of attacks and the consequences thereof. The solution is based upon employing an extension of the BGP FlowSpec protocol that allows the customer to decrease dramatically the harmful effect of the attack on its network. In addition to that, the customer is given a series of tools for blocking-out the undesired traffic from RASCOM’s network in order to avoid its propagation over the customer’s own network: black-holing (BGP-blackhole community), on-demand control of traffic filtering at the customer’s interface, customer’s personal account for independent controlling the FlowSpec filtering rules, connecting to the BGP FlowSpec controller for automatic mode filtering, FlowSpec rule’s function statistics.
Technical implementation
At RASCOM’s network, the protocol BGP FlowSpec (RFC5575) is fully introduced as an additional protection measure which allows to cut-off the traffic of those protocols and/or packet types that are not used at the customer’s network and are used in DDoS attacks.
The attacking traffic filtration is effected on the circuit and hardware resources level of RASCOM’s backbone network, immediately at all our backbone routers. The traffic as specified in the rules sent over the BGP FlowSpec, is either destroyed or rate-limited. The remaining traffic (that was not shown in the BGP FlowSpec rules) will be passed unaffected.
BGP FlowSpec Service is available in every Point of Presence of RASCOM’s IP network
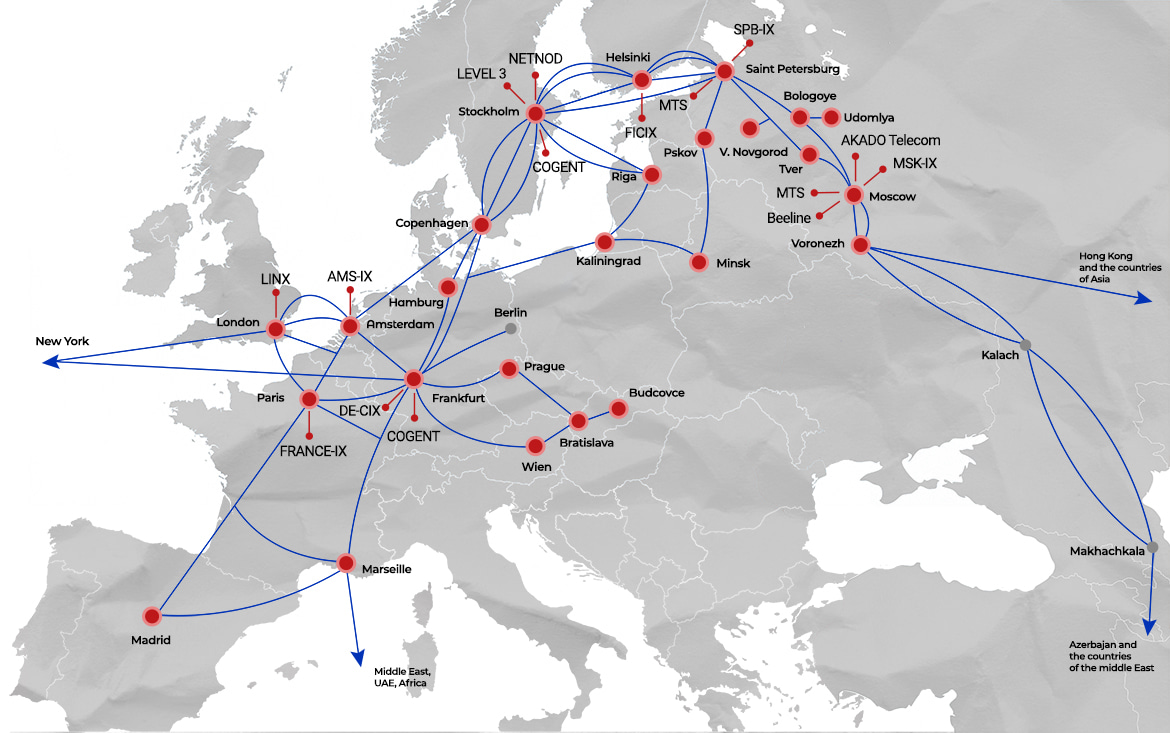
Service is available for following countries:
Russian Federation
Czech Republic
Poland
Latvia
Lithuania
Belarus
Sweden
Finland
Denmark
Germany
France
Great Britain
Netherlands
United States of America
Republic of China
Customer’s personal account
To establish filtration rules, the customer is given a WEB-interface in its personal account for those customers who have no opportunity to send the BGP FlowSpec protocol rules from their respective networks as well as for those whose network does not use BGP routing.
Along with that, in the account, statistics of using the filtration rules is available which makes it possible to estimate the efficiency of the protection measures.
BGP blackhole
As an additional measure for fighting against the attacks, a standard mechanism such as BGP blackhole community is used, as well. The BGP-Blackholing mechanism (Destination-based RTBH) is implemented using bgp-community for prefixes /32. That is, upon detecting any harmful traffic (an attack) on a host (IP-address) on the customer’s network, it is possible to announce over BGP to RASCOM the prefix of that host (/32) with a special blackhole-community 20764:6666, and the traffic toward the indicated host will be dropped at RASCOM’s network border by all backbone routers.
Service Technical Support and ACL installation
Service Technical Support and ACL installation can be ordered by sending a message to RASCOM’s NMC at: noc@rascom.ru
(phone: +7-812-702-2500). It is possible to install a filter (ACL) basing upon src/dst ip/proto/port at the connecting interface.
Link to BGP FlowSpec Service Presentation
To discuss technical and commercial terms of services provision, please, contact RASCOM Sales Department: +7(812)303-91-70 or +7(495)748-11-00.
To request the terms of the service in writing, please use the CONTACT FORM.